What's even worse: Most of those affected Android devices will probably never be patched.
Dubbed "Quadrooter," the set of four vulnerabilities discovered in devices running Android Marshmallow and earlier that ship with Qualcomm chip could allow an attacker to gain root-level access to any Qualcomm device.
The chip, according to the latest statistics, is found in more than 900 Million Android tablets and smartphones.
That's a very big number.
The vulnerabilities have been disclosed by a team of Check Point researchers at the DEF CON 24 security conference in Las Vegas.
Critical Quadrooter Vulnerabilities:
The four security vulnerabilities are:
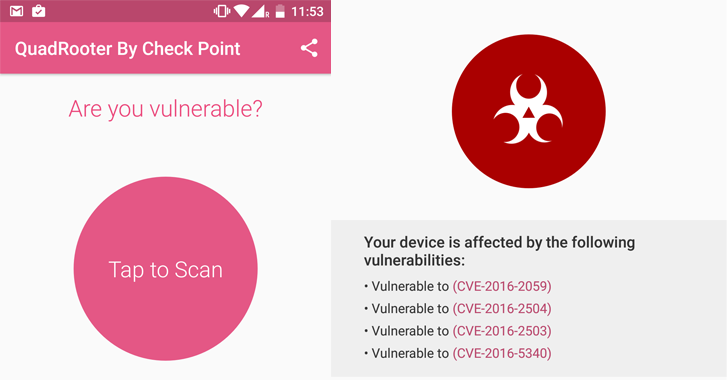
- CVE-2016-2503 discovered in Qualcomm's GPU driver and fixed in Google's Android Security Bulletin for July 2016.
- CVE-2016-2504 found in Qualcomm GPU driver and fixed in Google's Android Security Bulletin for August 2016.
- CVE-2016-2059 found in Qualcomm kernel module and fixed in April, though patch status is unknown.
- CVE-2016-5340 presented in Qualcomm GPU driver and fixed, but patch status unknown.
All an attacker needs is to write a piece of malware and send it to the victim. When installed, the malware offers the attacker privilege escalation on the affected devices.
According to the researchers, the attack can also be conducted through a malicious app. An attacker needs to trick a user into installing a malicious app that, unlike other malware, would execute without requiring any special permission checks.
"Such an app would require no special permissions to take advantage of these vulnerabilities, alleviating any suspicion users may have when installing," Check Point researchers write in a blog post.If any of the four vulnerabilities are successfully exploited, an attacker could gain root access to an affected device, giving the attacker full access to the device, including its data, camera and microphone.
List of Affected Devices (Popular)
Here's the list of some of the popular affected devices, though there are far more devices that are impacted by one or more Quadrooter vulnerabilities.
- Samsung Galaxy S7 and Samsung S7 Edge
- Sony Xperia Z Ultra
- OnePlus One, OnePlus 2 and OnePlus 3
- Google Nexus 5X, Nexus 6 and Nexus 6P
- Blackphone 1 and Blackphone 2
- HTC One, HTC M9 and HTC 10
- LG G4, LG G5, and LG V10
- New Moto X by Motorola
- BlackBerry Priv
How to Check if Your Device is Vulnerable?
You can check if your smartphone or tablet is vulnerable to Quadrooter attack using Check Point's free app.
Since the vulnerable software drivers, which control communication between Qualcomm chipset components, come pre-installed on these devices at the time of manufacturing, they can only be fixed by installing a patch from the devices' distributors or carriers after receiving fixed driver packs from Qualcomm.
"This situation highlights the inherent risks in the Android security model," the researchers say. "Critical security updates must pass through the entire supply chain before they can be made available to end users."Three of the four vulnerabilities have already been fixed in Google's latest set of monthly security updates, and a patch for the remaining flaw will be rolled out in the upcoming September update.
Since Qualcomm has already released the code, the phone manufacturers could be able to issue patches to the individual devices as soon as possible.
Android Nexus devices are already patched via the over-the-air updates, but other smartphone models will need to wait until their lazy phone manufacturers integrate the fixes into their own custom Android ROMs.
